概述
DLL远程注入
dll的注入和卸载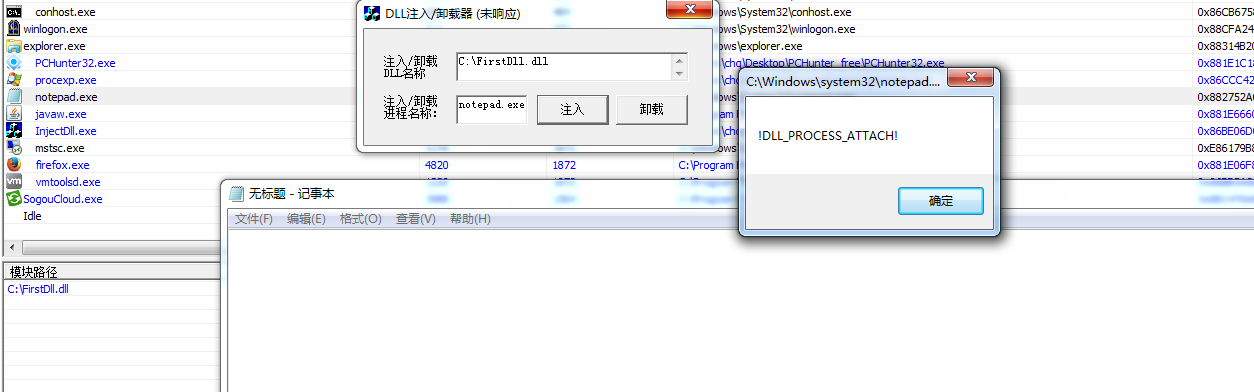
关键性代码如下:
1 | VOID CInjectDllDlg::InjectDll(DWORD dwPid, char *szDllName) |
整个注入与卸载的过程其实就是让远程线程执行一次LoadLibrary()函数或FreeLibrary()函数。
无DLL的代码注入
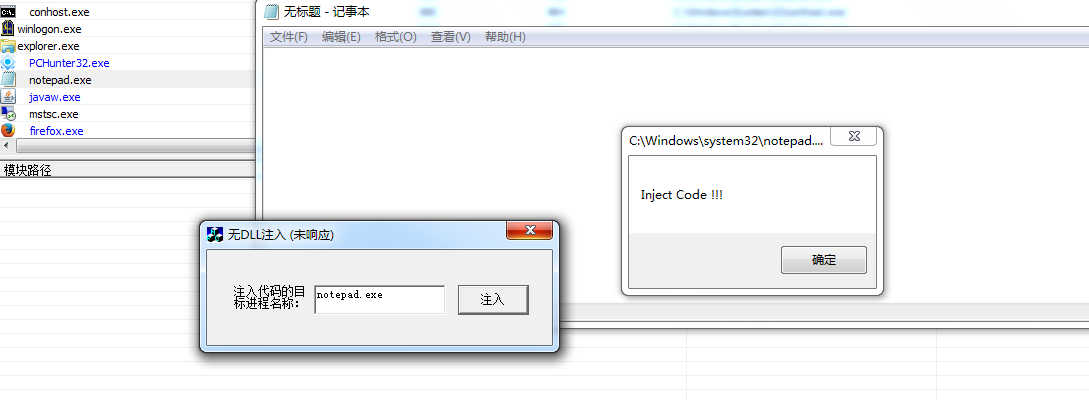
关键性代码:
1 | typedef struct _DATA |
通过peid可以查看DLL的导出函数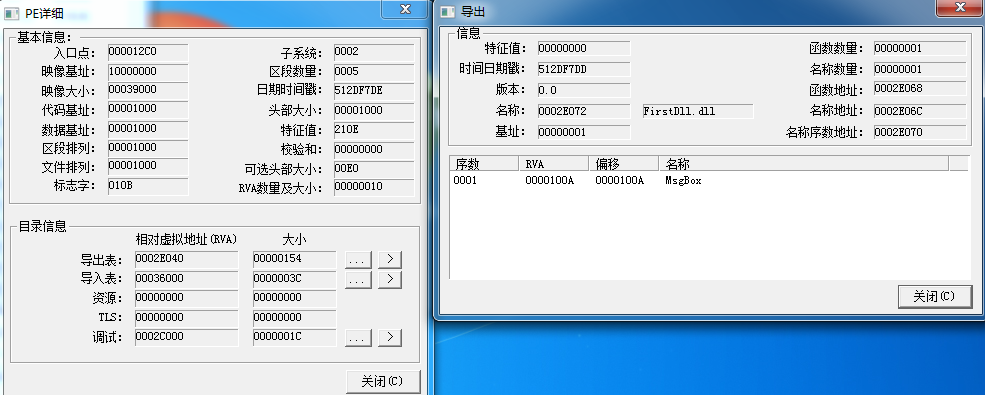
还可以通过vc6自带的dependency Walker以及CFF Explorer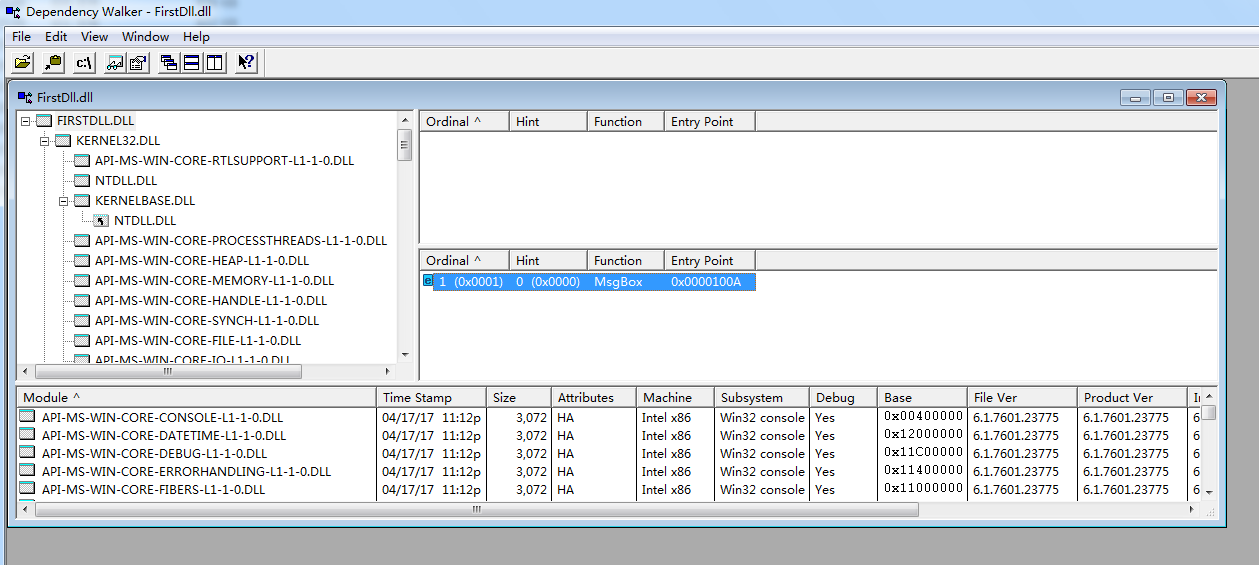
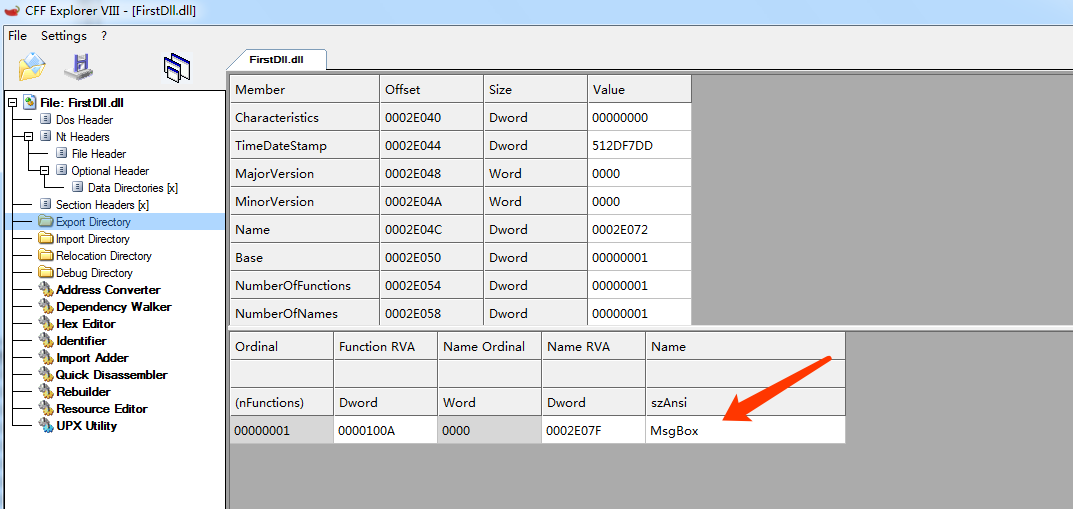
这种方式是直接把想要使用的API函数以及API函数所在的DLL文件都封装在一个结构体中,直接写入目标进程的空间中,最后调用CreateRemoteThread()函数即可将其运行。
tips
通过windows自带工具运行DLL的两种方法
1.通过regsvr32.exe 调用 例如 regsvr32 /i c:\test.dll
2.通过rundll32.exe 调用 例如 rundll32.exe “c:\test.dll” ,RundllFunc FunParam
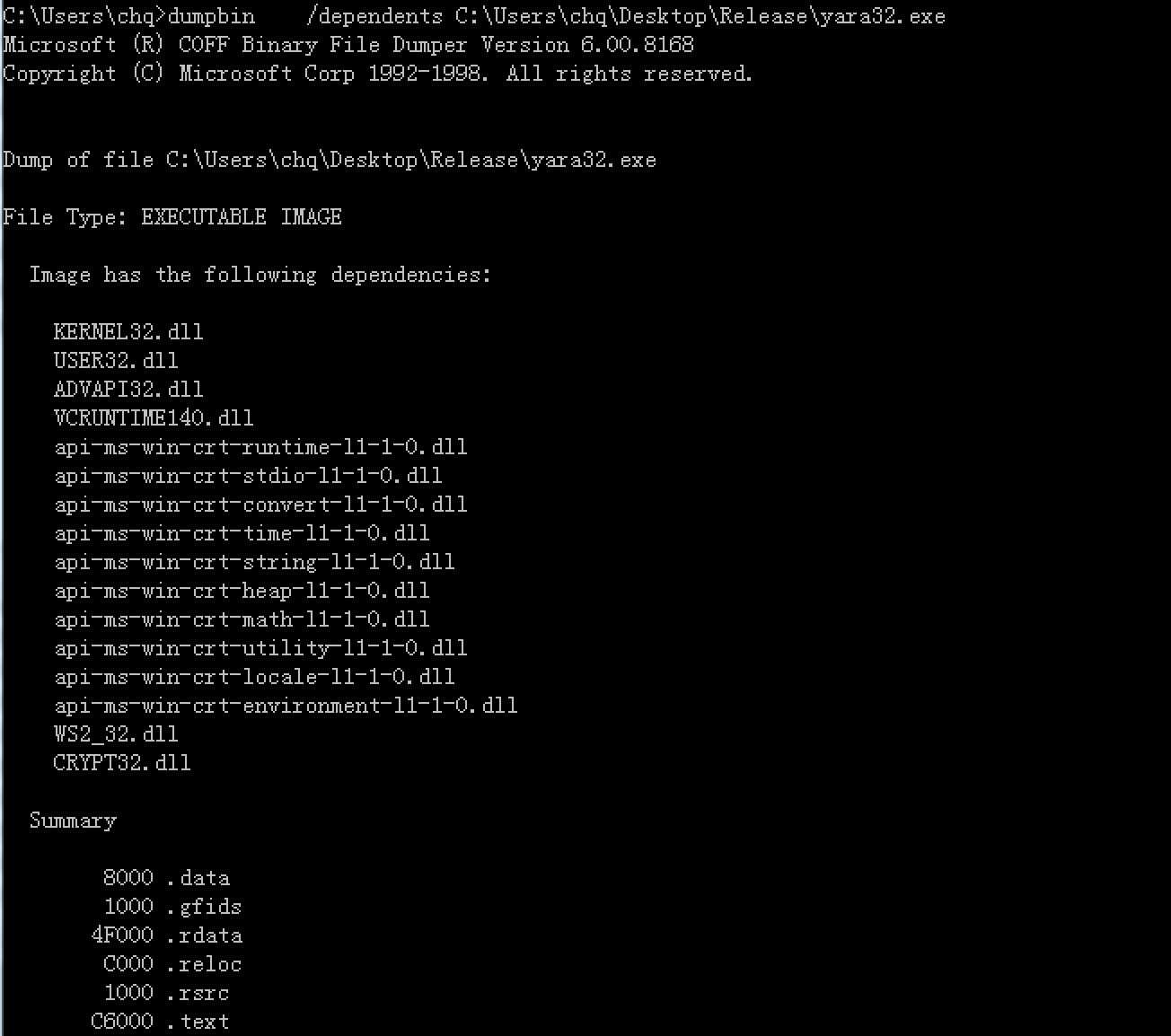
3.通过Dependency Walker工具查看应用程序所使用到的动态链接库文件,此外还可以使用dumpbin工具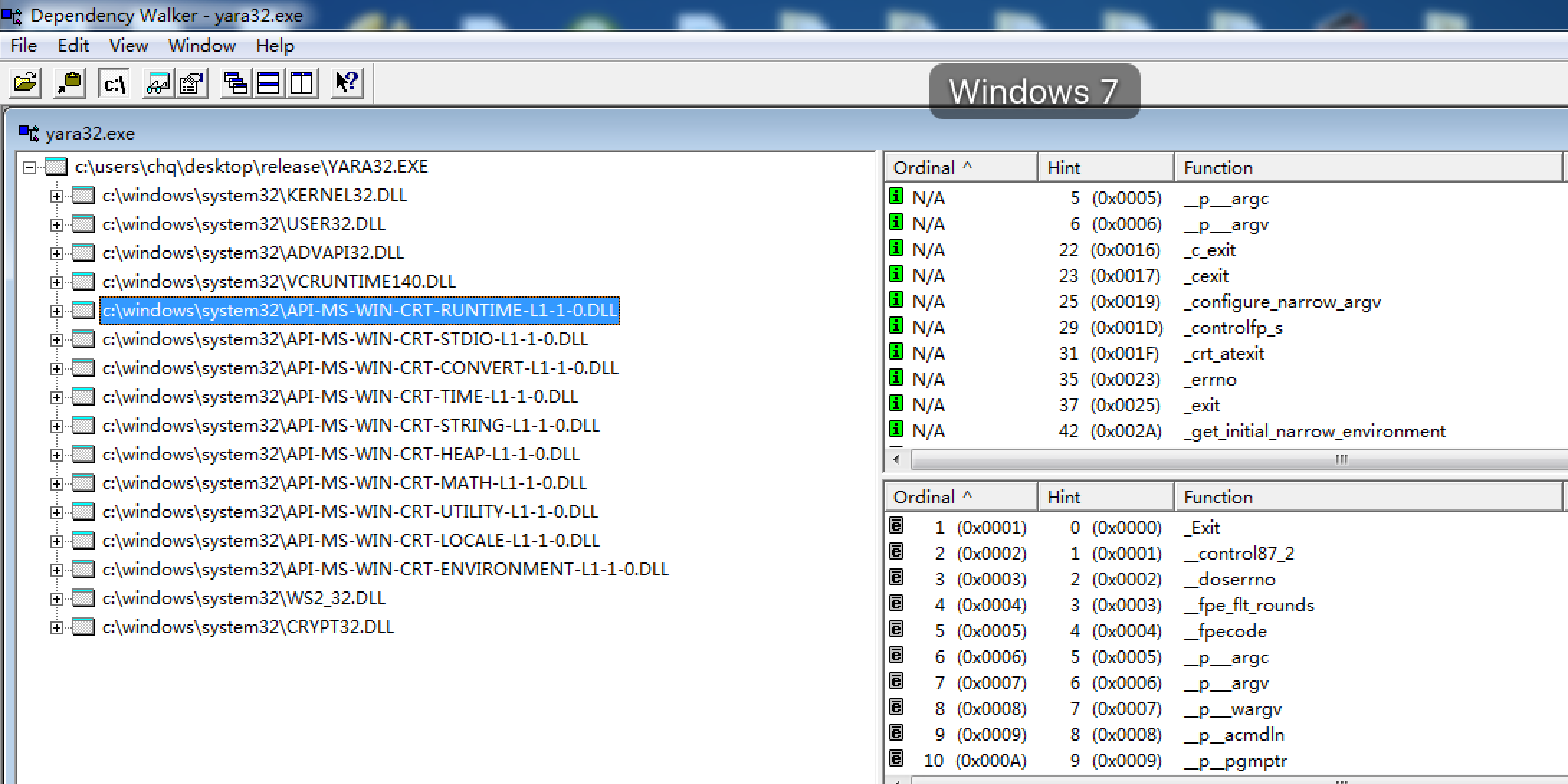
Reference
神奇的马甲Dll By 海风月影
DLL注入的几种姿势(二):CreateRemoteThread And More
windows进程注入